PCI compliance refers to whether a merchant adheres to the technical and operational requirements established by the PCI SSC to ensure safe handling of cardholder data.
The PCI SSC was established in 2006 when five of the major credit card brands—Visa, Mastercard, American Express, Discover, and Japan Credit Bureau—came together to create global standards for how companies should manage credit card data. Prior to this, each of the card brands maintained their own separate sets of requirements.
The PCI Data Security Standards (PCI DSS)—the rules established to govern how businesses manage cardholder data to ensure secure payment processing—are updated every three years (the most recent version being the PCI DSS 3.2.1). Rather than the PCI SSC, it’s the card brands and acquiring banks who are responsible for enforcing PCI compliance.
The PCI DSS requirements focus on these core elements of merchants’ business:
-
How merchants obtain and handle credit card data
-
How merchants store credit card data
-
How merchants continuously monitor security controls
What are the levels?
There are varying levels of PCI compliance requirements based on factors like the volume of credit card transactions your business processes annually. Here’s a breakdown of what each of these PCI levels entails.
Level 1
This is the highest level of security requirement, intended for merchants that process over 6 million credit card transactions every year.
Level 2
Intended for merchants that process between 1 and 6 million credit card transactions every year.
Level 3
Intended for merchants that process between 20,000 and 1 million e-commerce transactions every year.
Level 4
Intended for merchants that process fewer than 20,000 e-commerce transactions or up to 1 million total transactions (regardless of the payment acceptance channel) every year.
Self-Assessments
If a merchant experiences a data breach that results in account data being compromised, they may be required to adhere to a higher level of security requirements, regardless of how many card transactions they process.
Merchants within Level 1 must be assessed by a third party to be deemed compliant (through what’s known as a Qualified Security Assessor), whereas merchants in Levels 2 to 4 can self-evaluate their compliance through a Self-Assessment Questionnaire (SAQ).
To validate that your business is PCI-compliant, you’ll need to fill out an SAQ every year. The specific SAQ form you complete will depend on the environment you accept credit cards in (face-to-face, e-commerce, or by mail or telephone—also known as “card-not-present”) and the method used to transmit the information (e.g., via the internet or not). For every payment environment you support, you’ll fill out a separate SAQ. The pass mark for PCI compliance meets 100% of the criteria outlined in your respective SAQ.
There are 9 different SAQ forms:
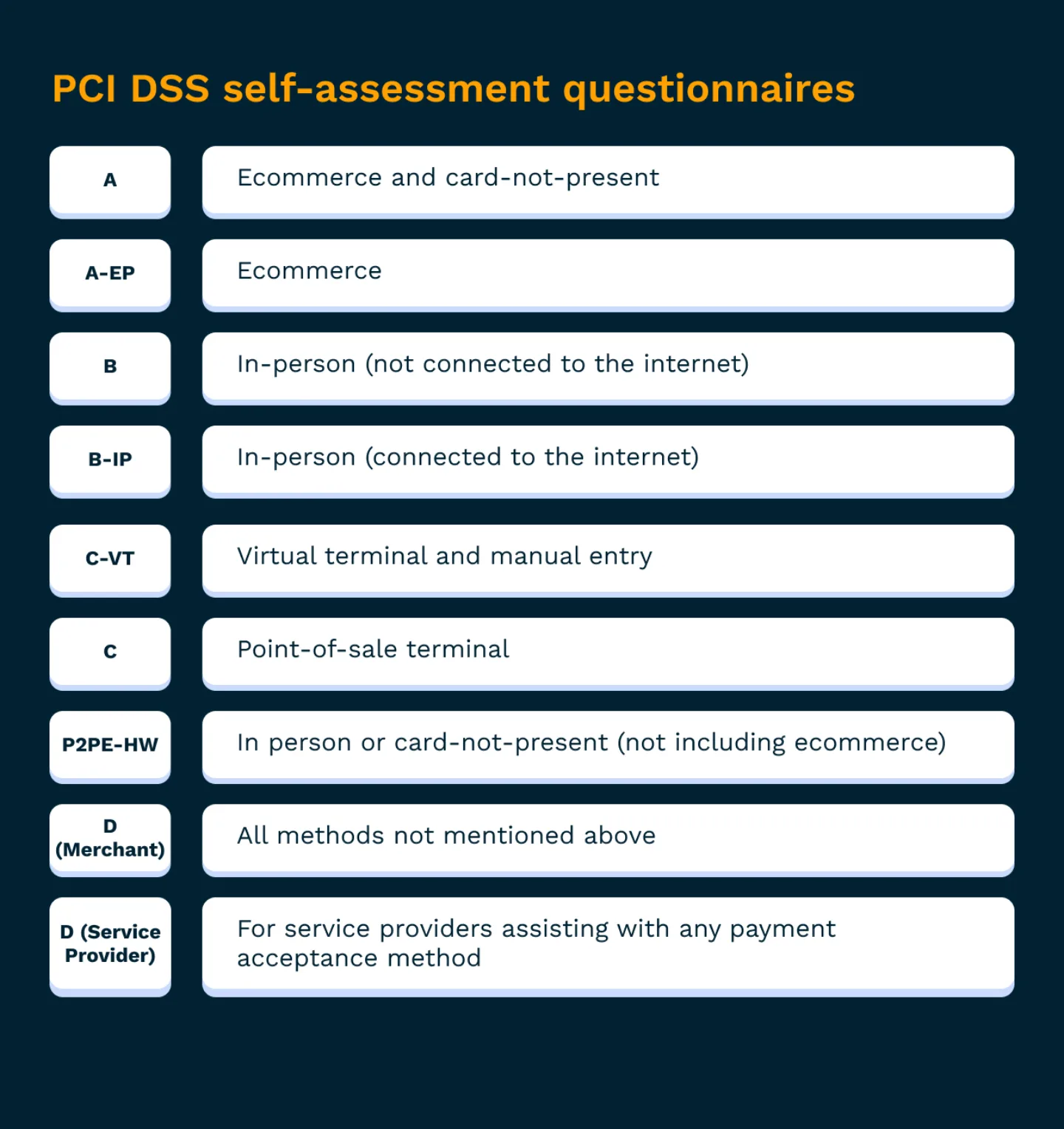
The nine types of SAQ forms. You’ll fill out a separate form for every method you use to accept payments.
Fines & Fees
The costs of falling victim to a data breach can be considerable. If a breach involving stolen credit card information is traced back to your business, then you’re on the hook for any fines and fees associated with it (such as covering the losses and card replacement costs).
The payment brands may, at their discretion, fine an acquiring bank $5,000 to $100,000 per month for PCI compliance violations. The banks will most likely pass this fine along until it eventually hits the merchant. Furthermore, the bank will also most likely either terminate your relationship or increase transaction fees. Penalties are not openly discussed nor widely publicized, but they can be catastrophic for small businesses.
What are the 12 PCI DSS requirements?
The PCI Data Security Standards cover 12 requirements that must be followed by any business that accepts or processes credit card payments. The PCI SSC groups these requirements into six unique buckets:
Build and maintain a secure network
- Install and maintain firewalls to protect cardholder data
- Do not use vendor-supplied defaults for system passwords and other security parameters
Protect cardholder data
- Protect stored cardholder data
- Encrypt transmission of cardholder data across any open or public network
Maintain a vulnerability management program
- Use and regularly update anti-virus software or programs
- Develop, maintain, and update secure systems and applications
Implement strong access control measures
- Restrict access to cardholder data by business need-to-know
- Assign a unique ID to each person with system access
- Restrict physical access to cardholder data
Regularly monitor and test networks
- Track and monitor all access to network resources and cardholder data
- Regularly test security systems and processes
Maintain an information security policy
- Maintain a policy that addresses information security for employees and contractors

